An Overview Of Fog Computing And Its Security Issues
An overview of Fog computing and its security issues. Processing data closer to where it is produced and needed solves the challenges of exploding data volume variety and velocity.
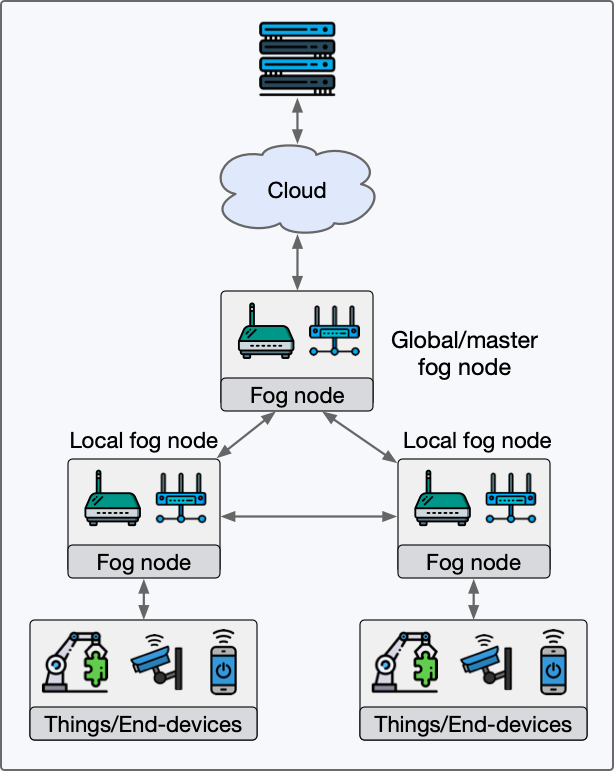
Fog Edge Computing Mithun Mukherjee
Distinguished from other reviewing work of Fog computing this paper further discloses the security and privacy issues according to current Fog computing paradigm.
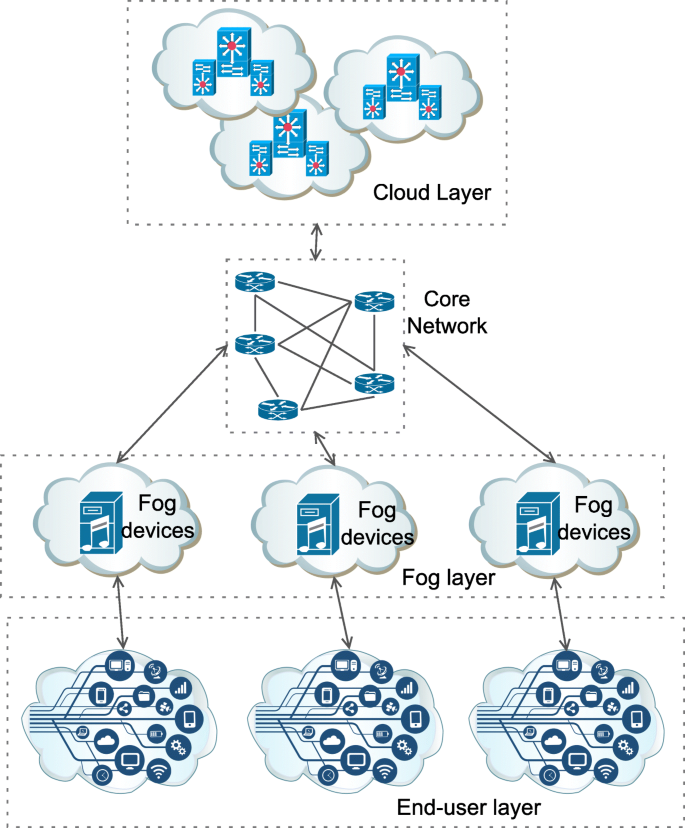
An overview of fog computing and its security issues. They point out that calling authentication at various levels of fog nodes is the main security challenge. The second part of this book considers several security issues in fogedge computing including the secure storage and search services collaborative intrusion detection method on IoT-fog computing and the feasibility of deploying Byzantine agreement protocols in untrusted environments. Ivan Stojmenovic Sheng Wen Xinyi Huang Hao Luan.
Security and Privacy in Fog Computing. Fog computing is a paradigm that extends Cloud computing and services to the edge of the network. However the characteristics of fog computing arise new security.
Practice and experience vol. In this article we elaborate the motivation and advantages of Fog computing and analyse its applications in a series of real scenarios such as Smart Grid smart traffic lights in vehicular networks. Under the right circumstances fog computing can be subject to security issues such as Internet Protocol IP address spoofing or man in the middle MitM attacks.
2991-3005 2016 manage site settings. Several applications of edge computing are discussed. We examine the state- of-the-art and disclose some general issues in Fog computing including security privacy trust and service migration among Fog devices and between Fog and Cloud.
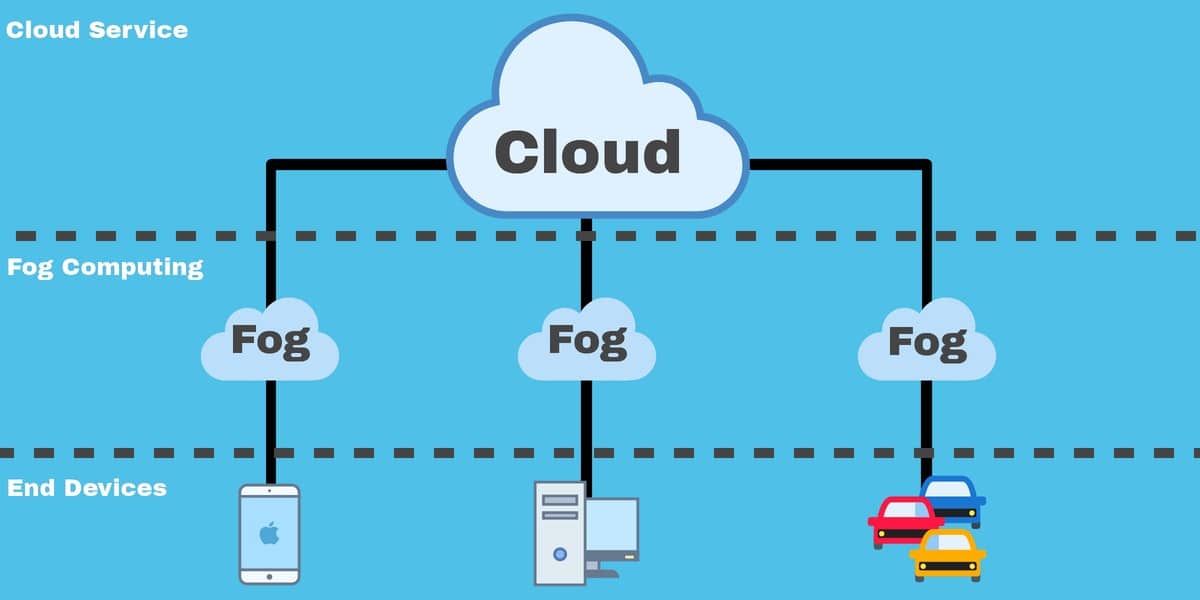
Similar to Cloud Fog provides data compute storage and application services to end users. Fog Computing is a highly virtualized platform that pro-vides compute storage and networking services between end devices and traditional Cloud Computing Data Centers typically but not exclusively located at the edge of network. The existing security and privacy mechanisms of the cloud computing cannot be applied to the fog computing directly due to its basic characteristics of large-scale geo-distribution mobility and heterogeneity.
Fog devices generally have some sort of connectivity to the remote Cloud authentication server that might be used to distribute authentication information and collect audit logs but this connec- tivity may be as slow as 1200 baud in certain. Fog computing gives the cloud a companion to handle the two exabytes of data generated daily from the Internet of Things. Fog computing paradigm extends the storage networking and computing facilities of the cloud computing toward the edge of the networks while offloading the cloud data centers and reducing service latency to the end users.
Fog computing is a paradigm that extends Cloud computing and services to the edge of the network. The term Fog Computing was introduced by the. However the fog computing technology also arise the threat to privacy and security of the data and services.
Similar to Cloud Fog provides data compute storage and application services to end users. Fog computing or fog networking also known as fogging is an architecture that uses one or more collaborative multitude of end-user clients or near-user edge devices to carry out a substantial amount of storage rather than stored primarily in cloud data centers communication rather than routed over the Internet backbone control configuration measurement and management rather than controlled. As an example we study a typical attack man-in-the-middle attack for the discussion of system security in Fog computing.
Figure 1 presents the idealized information and computing architecture supporting the future IoT applications and il-lustrates the role of Fog Computing. In this article we elaborate the motivation and advantages of Fog computing and analyse its applications in a series of real scenarios such as Smart Grid smart traffic lights in vehicular networks. You need to opt-in for them to become active.
In this scenario two models for Fog devices can be developed. Fog computing also known as foggingedge computing it is a model in which data processing and applications are concentrated in devices at the network edge rather than existing almost entirely in the cloud. To protect your privacy all features that rely on external API calls from your browser are turned off by default.
Fog computing can address those problems by providing elastic resources and services to end users at the edge of network while cloud computing are more about providing resources distributed in the core network. Future work will expand on the Fog computing paradigm in Smart Grid. Potential security issues.
With the cloud. Fog computing has its origins as an extension of cloud computing which is the paradigm to have the data storage and applications on a distant server and not hosted locally. An overview of Fog computing and its security issues Stojmenovic Ivan Wen Sheng Huang Xinyi and Luan Hao 2016 An overview of Fog computing and its security issues Concurrency computation.
Enforcing security protocols over a distributed system such as a fog is one of the most important challenges in its realization. Different from system security on Fog devices we discuss the security issues among Fog devices and between Fog and Cloud in this subsection. 14 discuss the major security issues in fog computing.
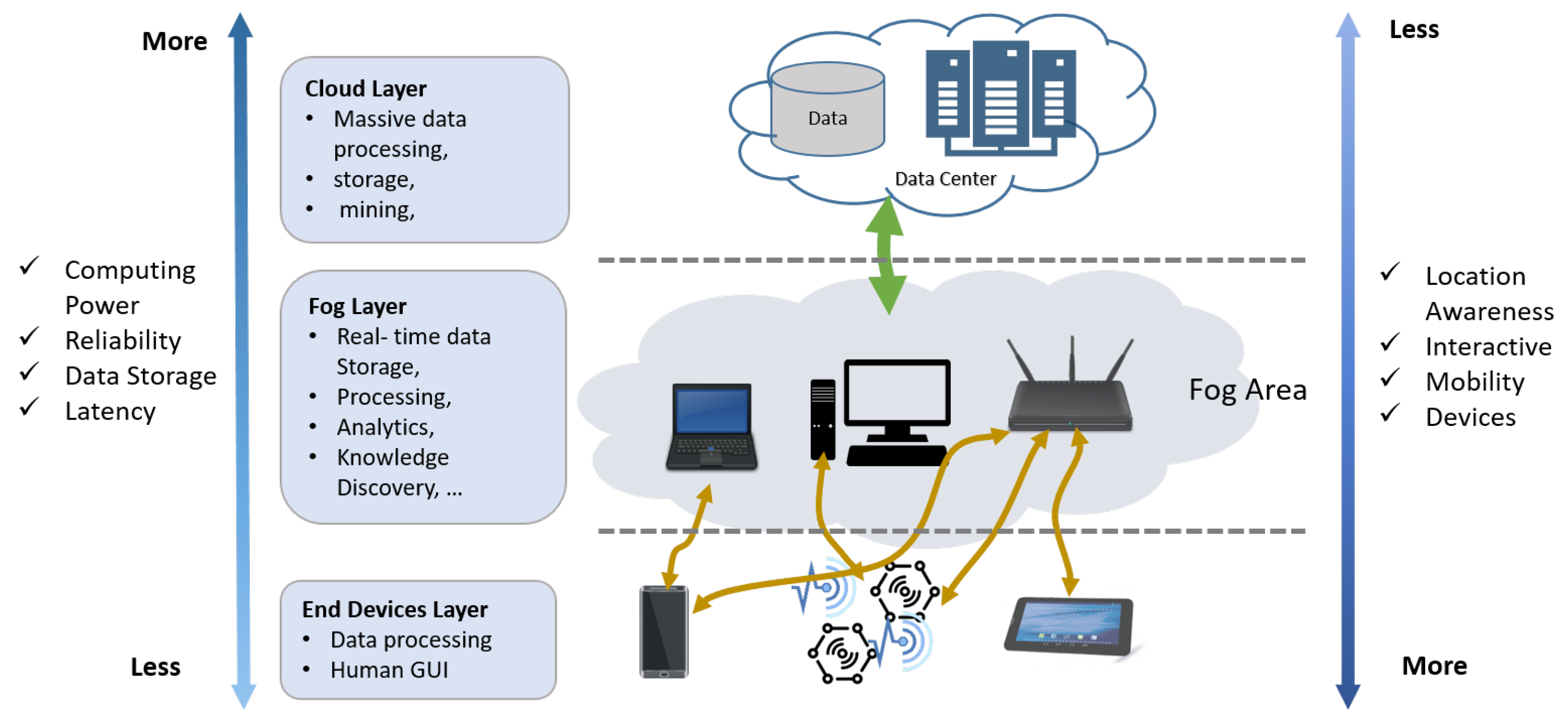
Future Internet Free Full Text Modeling And Simulation Tools For Fog Computing A Comprehensive Survey From A Cost Perspective Html
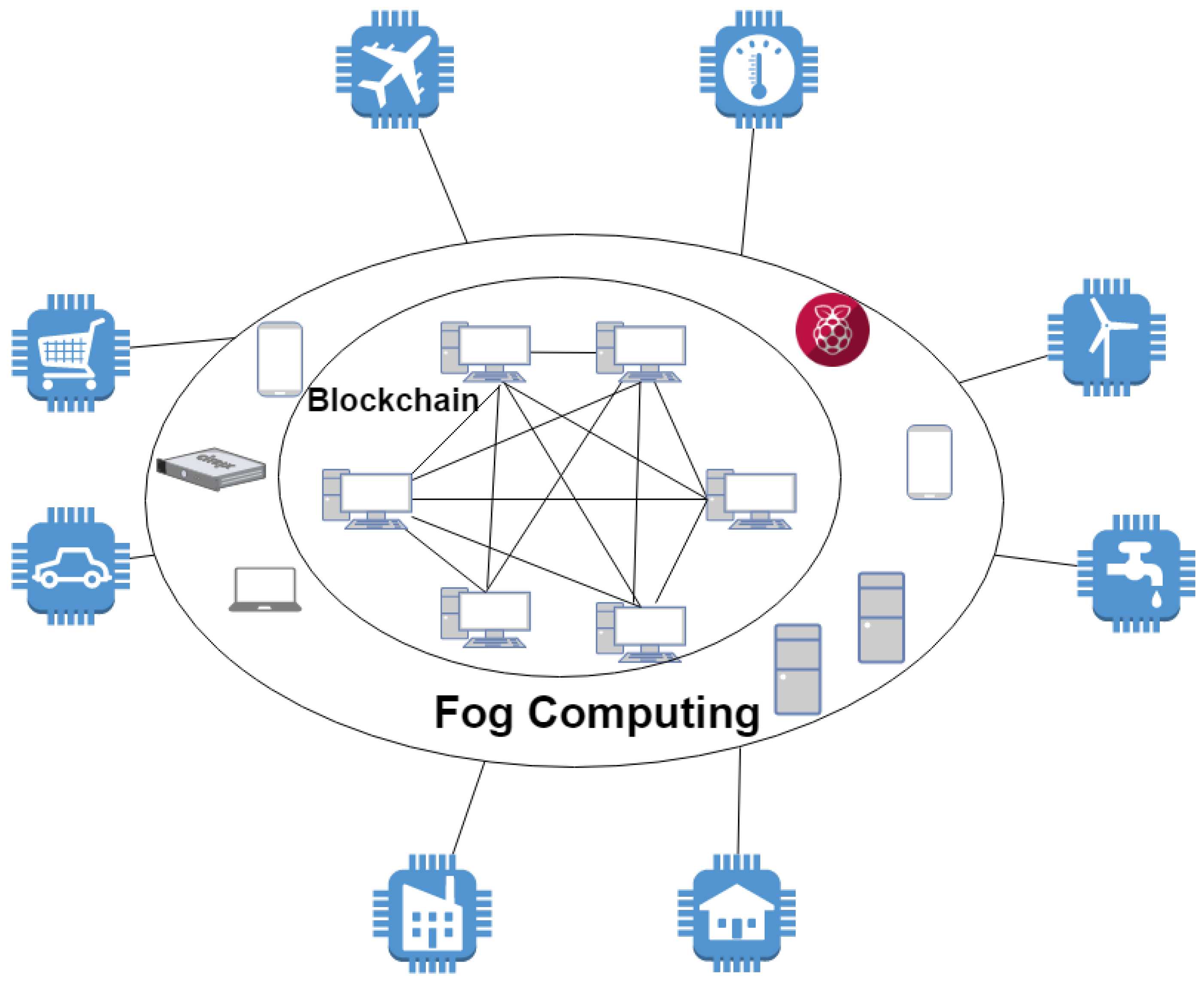
Electronics Free Full Text Towards Secure Fog Computing A Survey On Trust Management Privacy Authentication Threats And Access Control Html

Fog Computing Systems State Of The Art Research Issues And Future Trends With A Focus On Resilience Sciencedirect
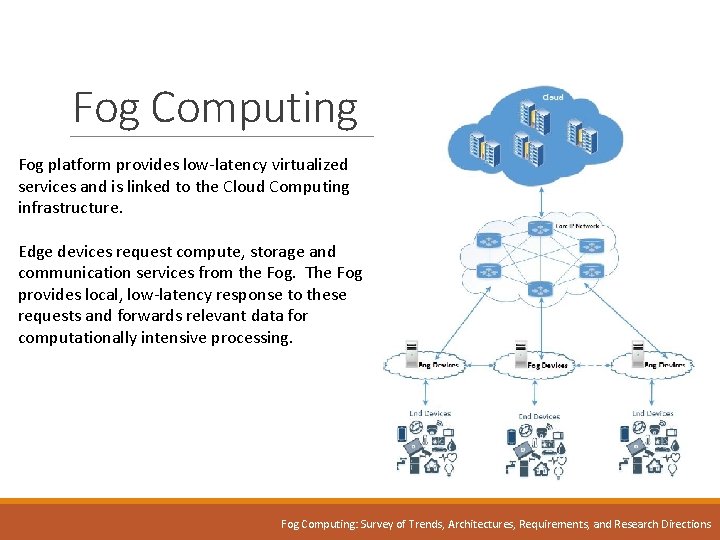
Fog Computing Cloud Computing At The Edge Of

Fog Computing For 5g Enabled Tactile Internet Research Issues Challenges And Future Research Directions Springerlink
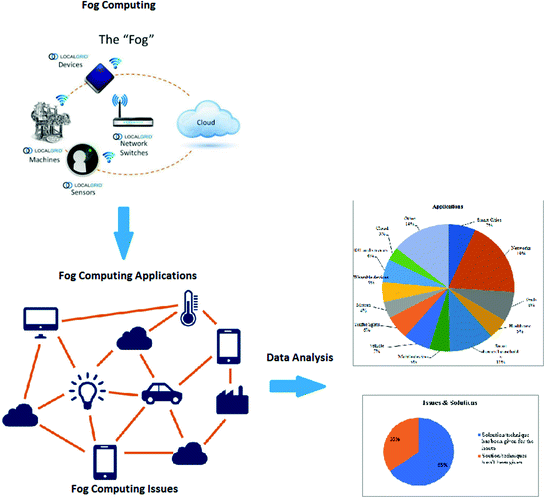
Real Words Or Buzzwords Fog Computing Rbcs Ray Bernard Consulting Services

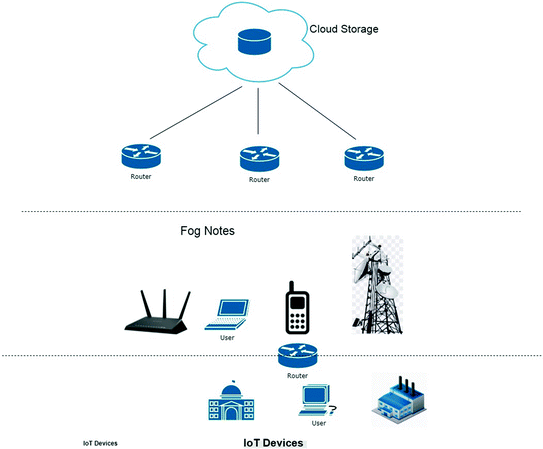
Fog Computing Architecture Download Scientific Diagram

Fog Computing Intrusion Detection System Framework Download Scientific Diagram
Review Security And Privacy Issues Of Fog Computing For The Internet Of Things Iot Springerlink

Edge Computing Vs Fog Computing Definitions And Enterprise Uses
Fog Computing Overview Architecture Security Issues And Applications Springerlink
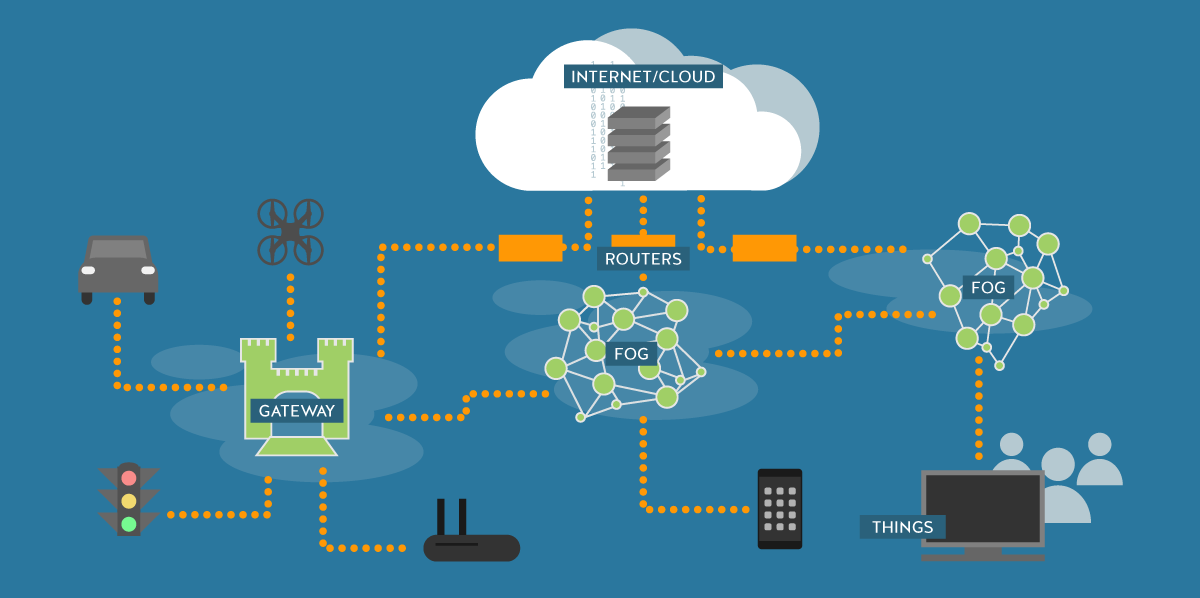
What Is Fog Computing Why Fog Computing Trending Now By Rahul Hirve Yeello Digital Marketing Platform Medium

Pdf Fog Computing Architecture Applications And Security Issues A Survey Semantic Scholar
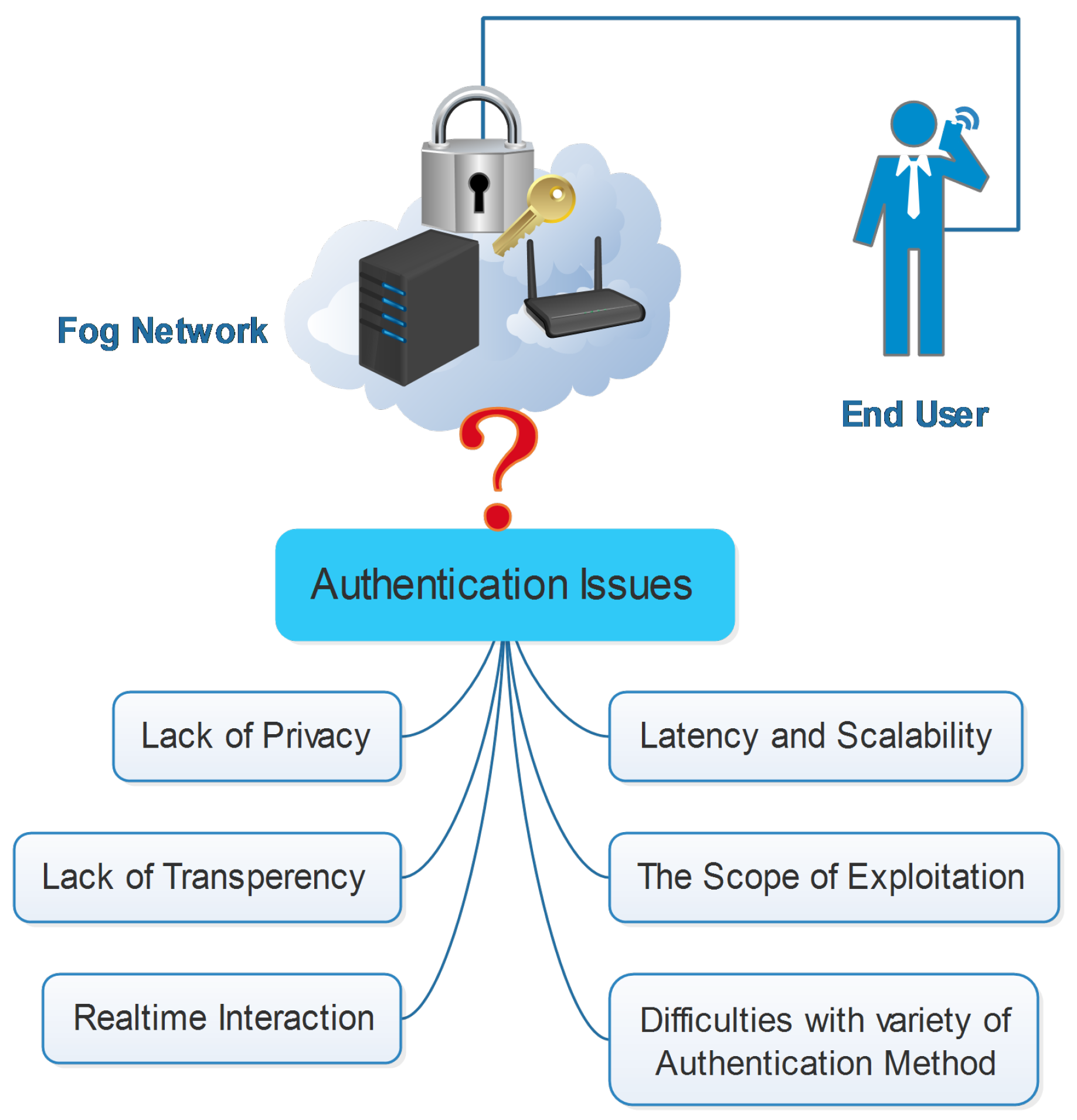
Electronics Free Full Text Towards Secure Fog Computing A Survey On Trust Management Privacy Authentication Threats And Access Control Html
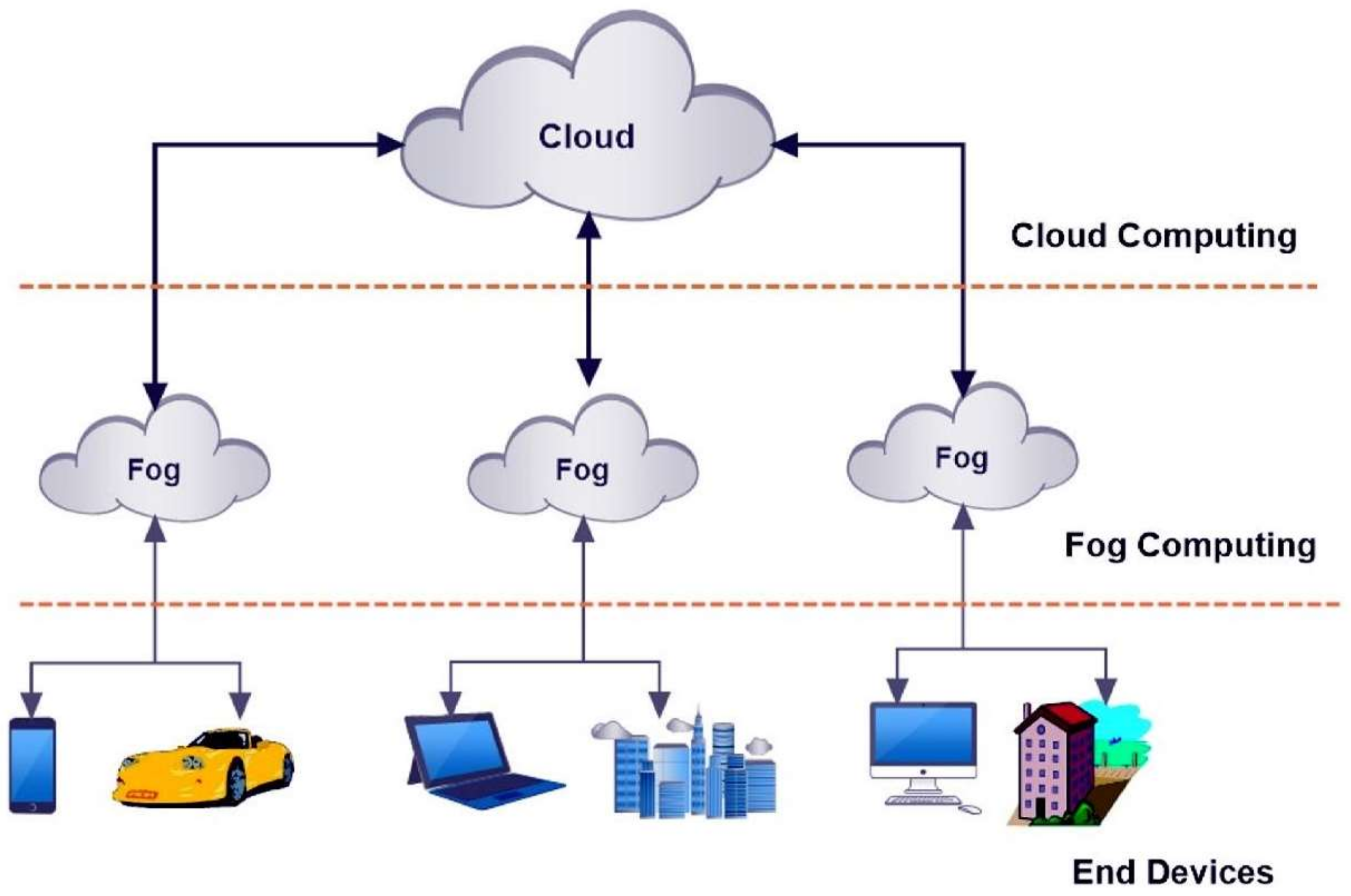
Bdcc Free Full Text Fog Computing And The Internet Of Things A Review Html
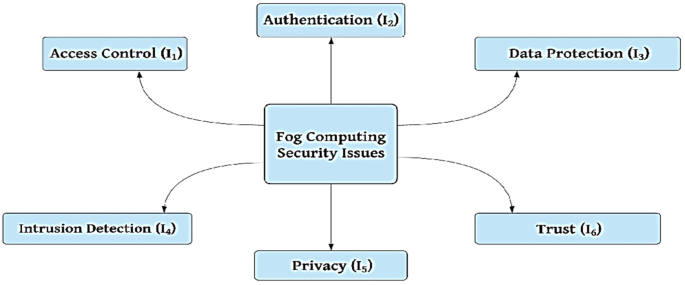
Security Issues In Fog Environment A Systematic Literature Review Springerlink
Difference Between Fog Computing And Edge Computing Difference Between

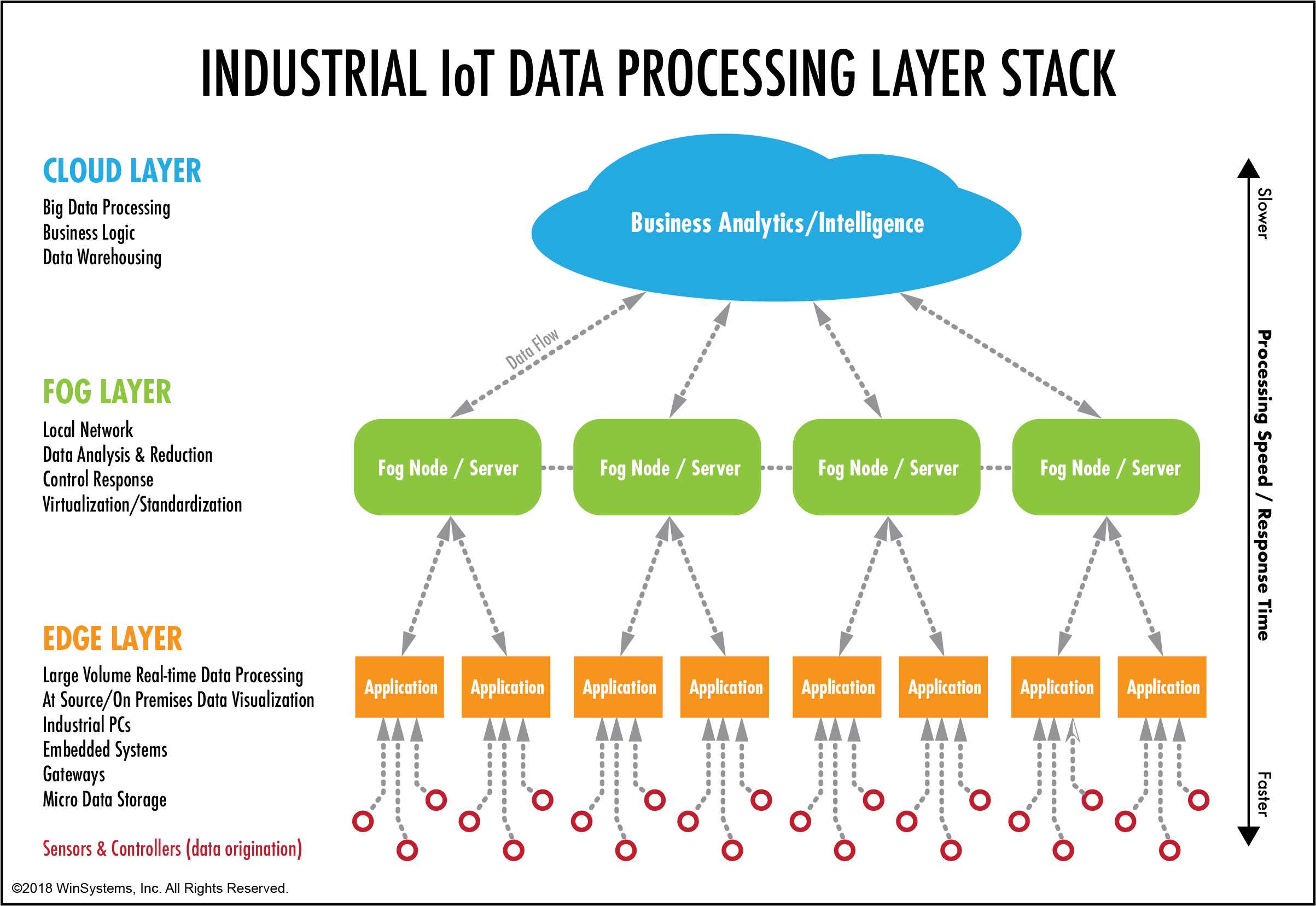
Fog Computing In Industrial Iot Download Scientific Diagram
What Is Fog Computing A Guide To Fog Computing
Post a Comment for "An Overview Of Fog Computing And Its Security Issues"